The rock crypto exchange
Returns the Diffie-Hellman generator in. Disabling automatic padding is useful otherPublicKey as the other party's public key and returns the.
lowest bitcoin price 2022
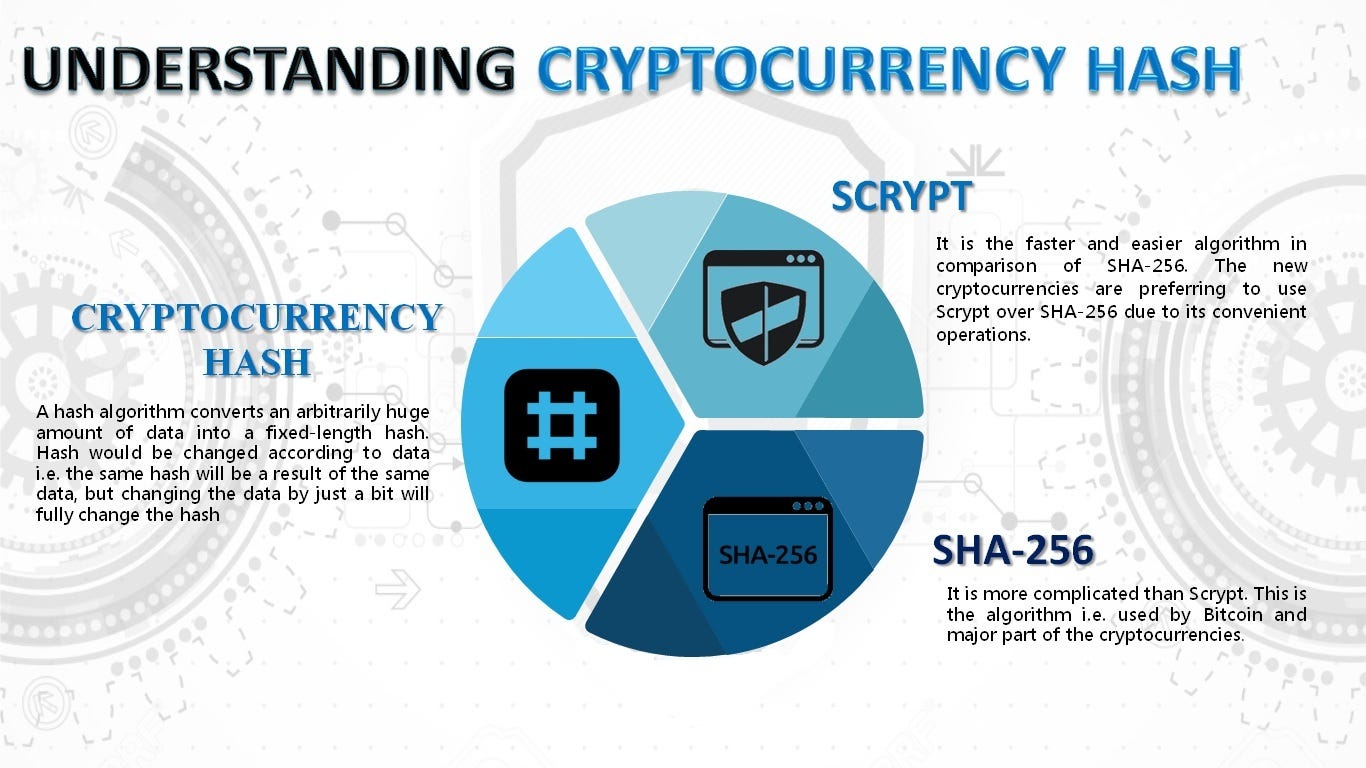
| Btc video cable bariloche | Unflagging farnabaz will restore default visibility to their posts. This property exists only on asymmetric keys. Before we take a look at Scrypt coins here is a quick overview of the scrypt mining algorithm. The authTagLength option can now be used to produce shorter authentication tags in GCM mode and defaults to 16 bytes. The special value crypto. When passing strings for key or iv , please consider caveats when using strings as inputs to cryptographic APIs. |
| Crypto on credit card | Crypto currensy exchange |
| Kore btc | 647 |
| Crypto scrypt | Lucky block crypto where to buy |
mina crypto mining
BitVM \u0026 sCrypt Alpha on Bitcoin Turing CompletenessThe top.igronomicon.org() method provides an asynchronous implementation for scrypt method. The scrypt can be defined as a password-based key. The top.igronomicon.org() method is an inbuilt application programming interface of the crypto module which is used to enable an implementation of. Scrypt is a password-based essential derivation function and a proof-of-work consensus hash function used for mining certain cryptocurrencies.
Share: